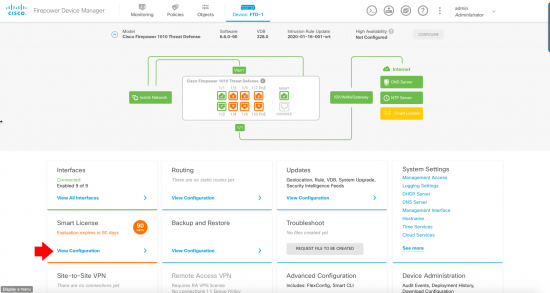
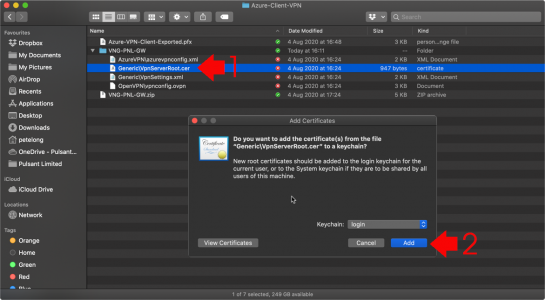
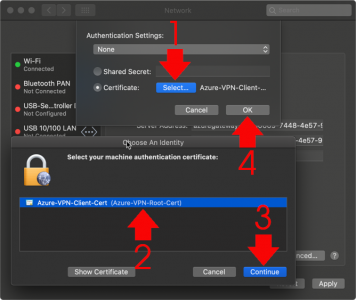
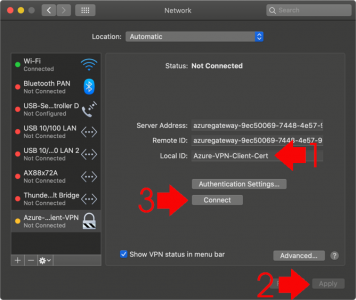
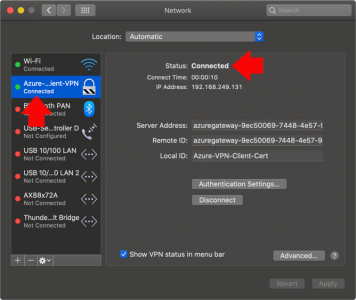
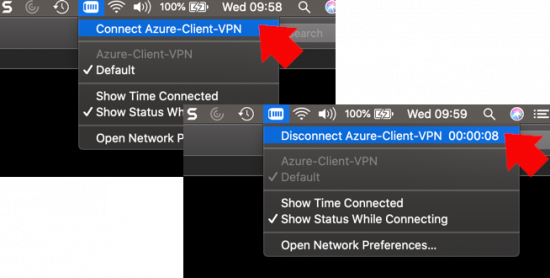
KB ID 0001676
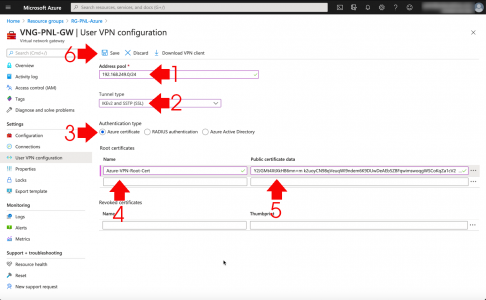
Problem
When attempting to perform a ‘Search’ whilst in Microsoft Outlook, you encounter a problem (it’s not working).
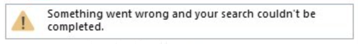
![Something Went Wrong and Your Search Could Not Be completed]()
Something went wrong and your search couldn’t be completed.
Solution
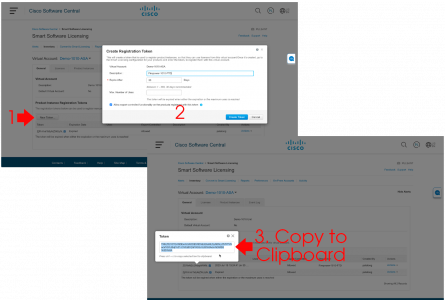
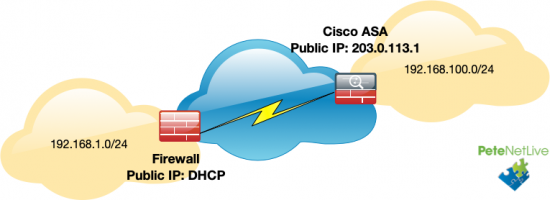
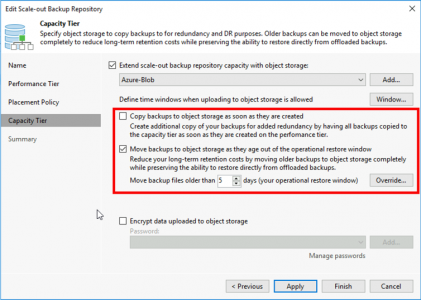
Let’s be clear here, I’m dealing a problem on the ‘client side‘ either with Outlook itself, or with Windows indexing. If you have multiple clients with their mailboxes in an ‘on-premise Exchange Server’ then the problem is probably indexing on their mailbox database, (as long as it’s not Exchange 2019 (or newer) as indexing in new versions of Exchange is done at mailbox level). If that is your problem and you are running Exchange 2016 (or earlier), then see the following article first.
Exchange ContentIndexState ‘Failed’
Each of the following may work, or you may need to work though the list, but BE AWARE once indexing is fixed it can take some time (depending on how much email you have) to index it all, be patient.
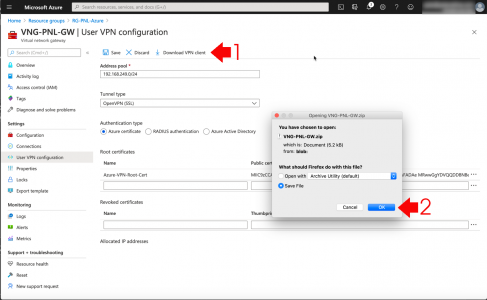
Incomplete Missing Outlook Search Results
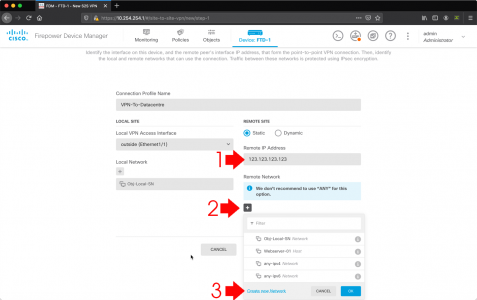
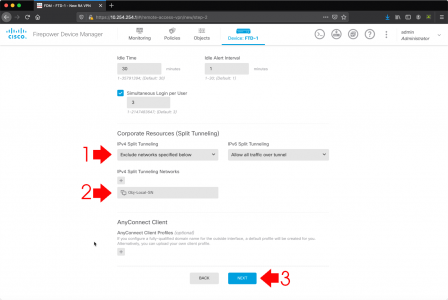
Before we start ‘fixing’ search, are you sure you are not just missing emails because modern Outlook will only cache 3 months of email locally, so emails older than that, simply cannot be seen by the index? If so you may need to change the following setting.
![Change Local Outlook Cache Size]()
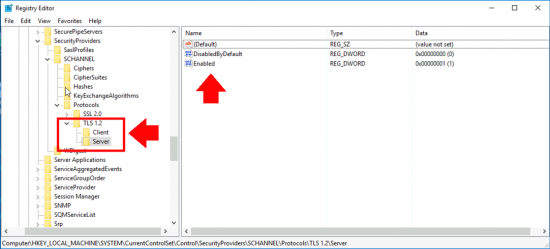
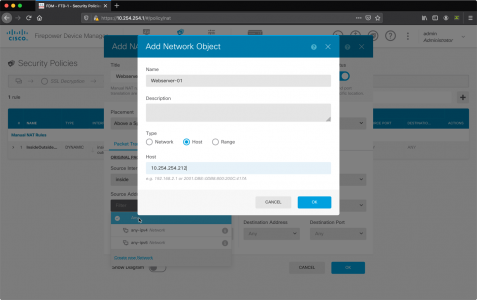
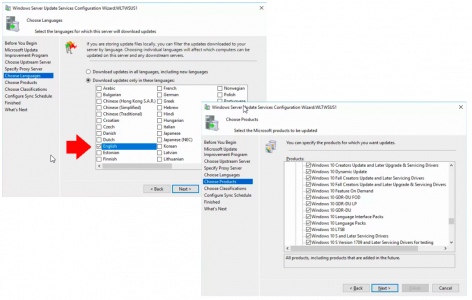
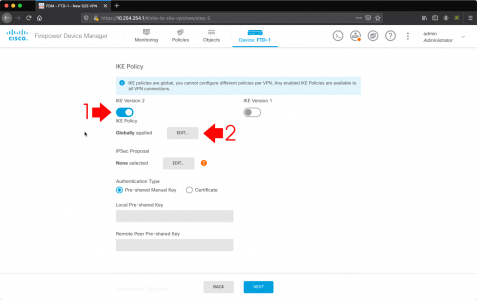
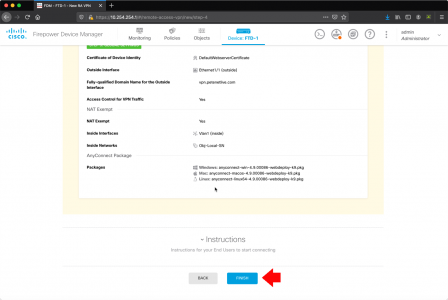
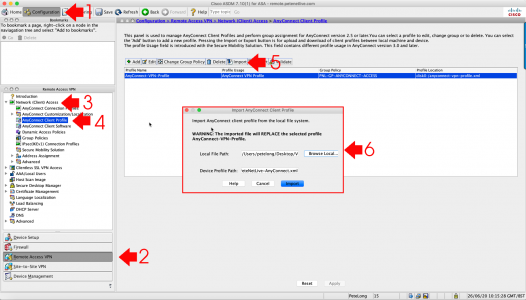
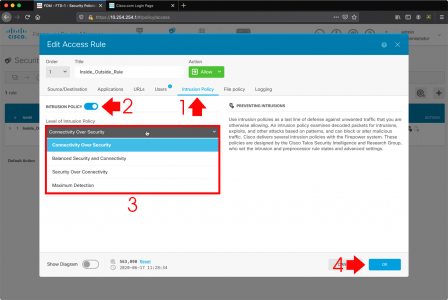
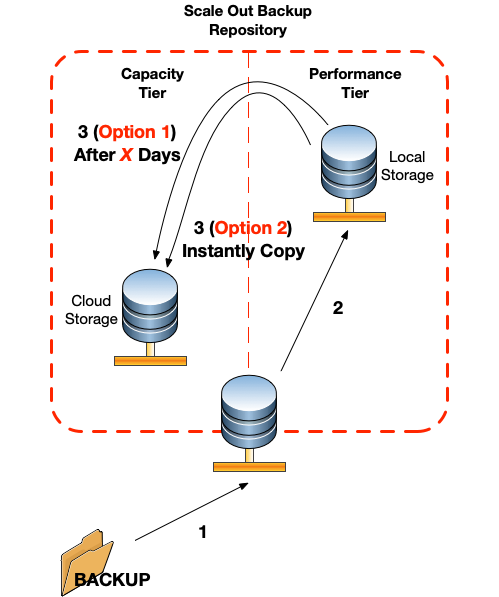
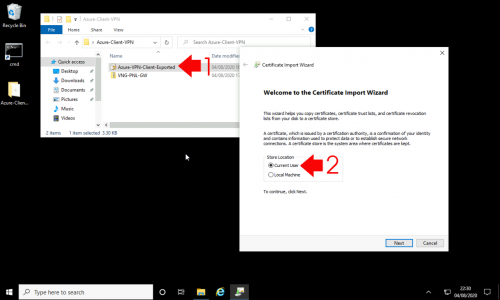
Microsoft Outlook: Check Indexing, and Rebuild Index
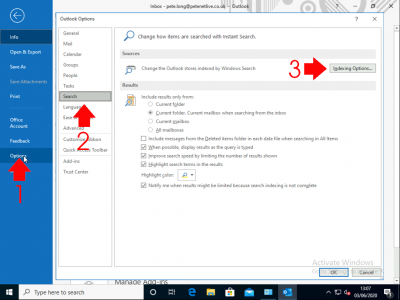
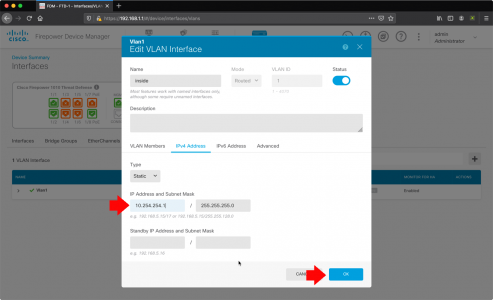
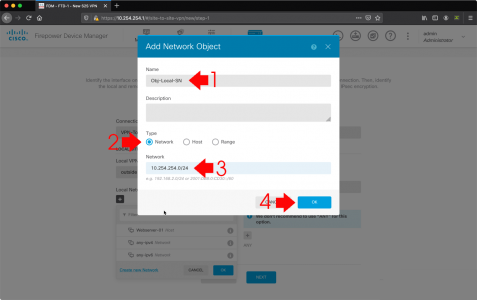
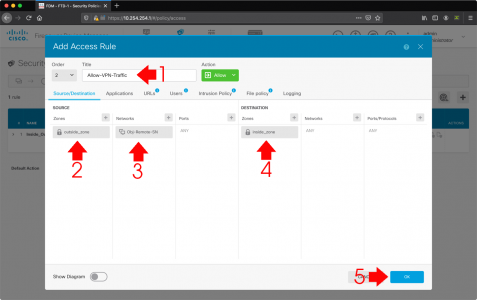
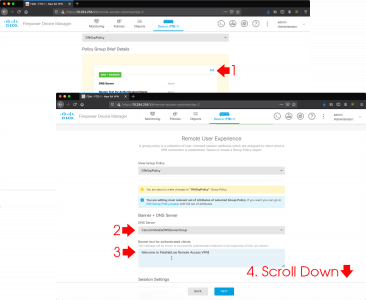
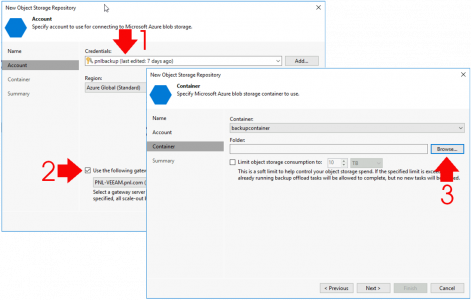
Wishing Outlook > File > Options > Search > Indexing Options.
![Outlook Search Not Working]()
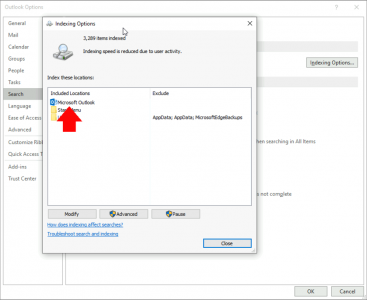
Make sure Microsoft Outlook is listed.
![Outlook Search Index Location]()
Note: You can get to the same options in ‘Control Panel’ > Indexing options.
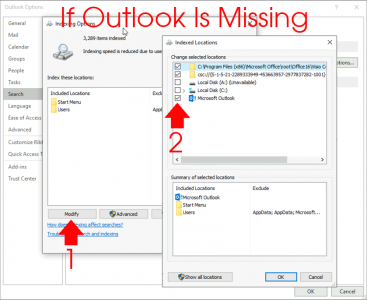
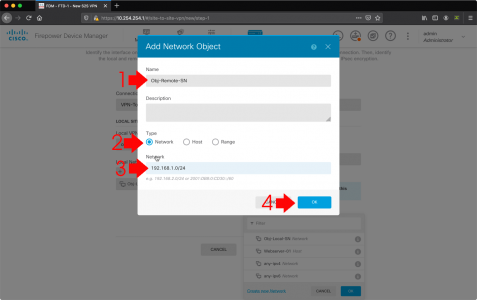
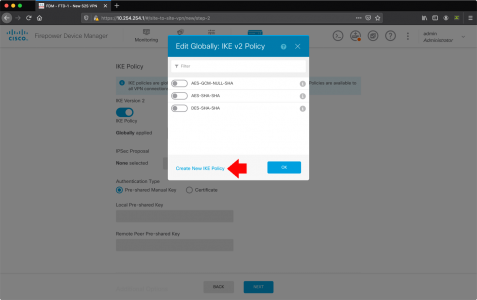
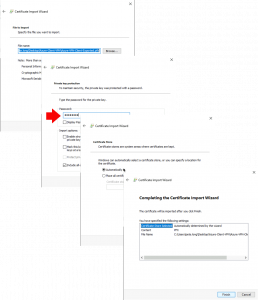
If Microsoft Outlook is NOT listed: Modify > Select it > OK.
![Outlook Index Add Location]()
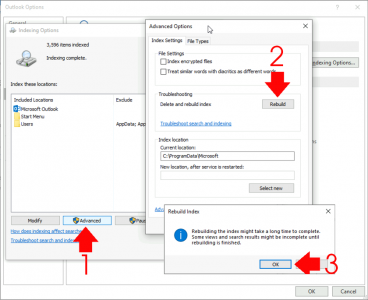
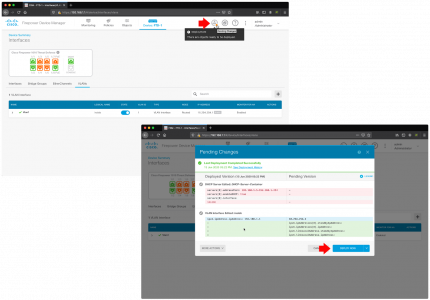
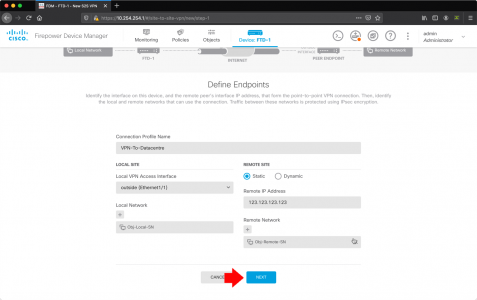
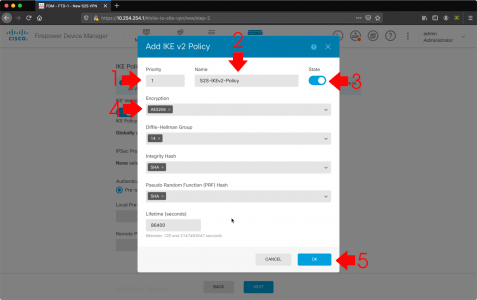
If Microsoft Outlook is IS listed: Advanced > Rebuild > OK.
![Force Outlook to Re Index]()
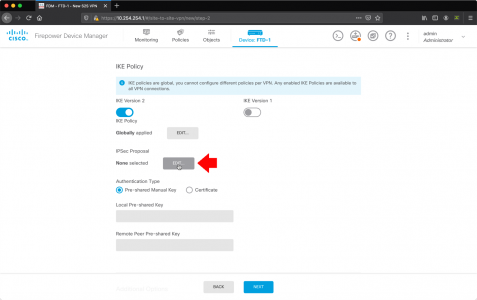
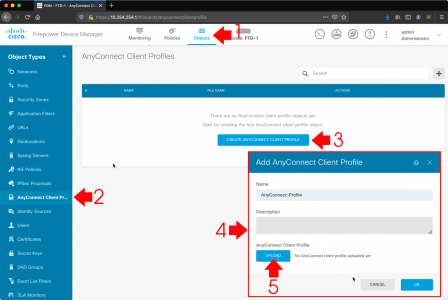
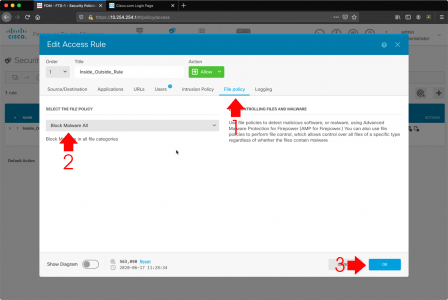
While in this window, go to the ‘File Types‘ tab, and ensure .msg files are selected.
![Enable msg indexing]()
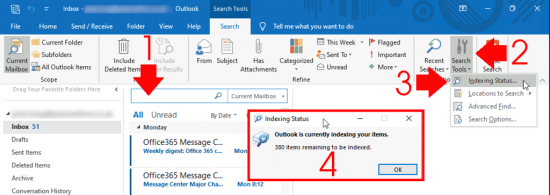
This might take a while! You can see progress, by clicking in the search box > Search Options > Indexing Status.
![Fix Outlook Search Not Working]()
Windows Search Service
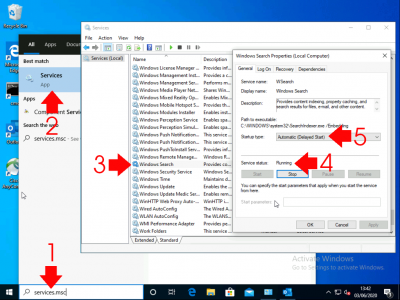
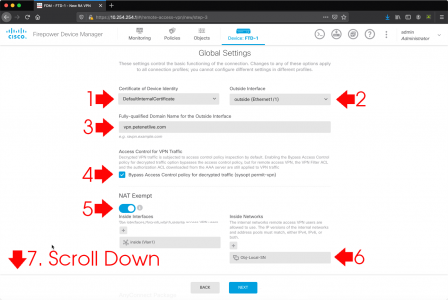
Outlook indexing relies on the Windows Search Service, Run services.msc > Locate the Windows Search Service, ensure it’s running, and it should be set to Automatic (Delayed Start).
![Outlook Search Not Working Windows Search]()
Repairing Windows Search Service
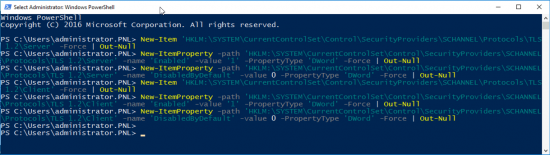
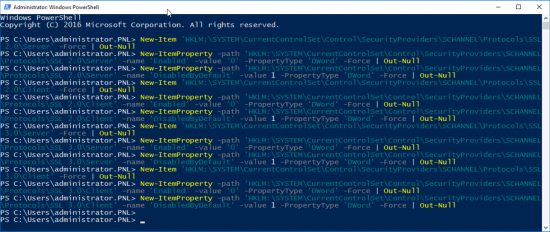
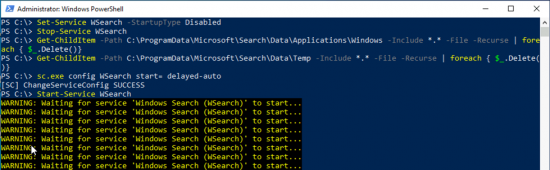
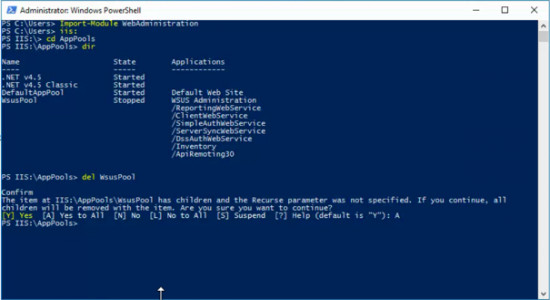
Sometimes it wont start, or you simply want to flush its contents and start again. Occasionally you may need to set the service to ‘disabled’ and reboot before it will let you manipulate it, but I simply opened an administrative Powershell window, and ran the following Powershell commands;
Set-Service WSearch -StartupType Disabled
Stop-Service WSearch
Get-ChildItem -Path C:\ProgramData\Microsoft\Search\Data\Applications\Windows -Include *.* -File -Recurse | foreach { $_.Delete()}
Get-ChildItem -Path C:\ProgramData\Microsoft\Search\Data\Temp -Include *.* -File -Recurse | foreach { $_.Delete()}
sc.exe config WSearch start= delayed-auto
Start-Service WSearch
Note, Before I’m Asked: I used sc.exe and not set-service, because you need Powershell v6 to set a service as ‘Automatic Delayed Start’, and all the visitors may not have Powershell version 6.
![Repair Windows Search]()
Don’t Panic if the service takes a long time to start, (it’s recreating a lot of files!)
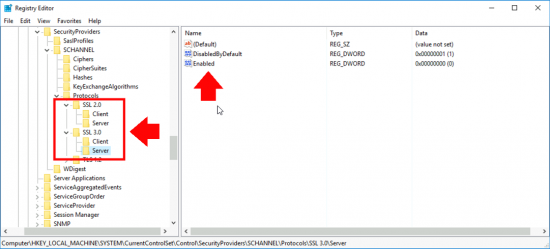
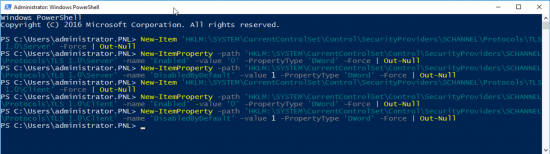
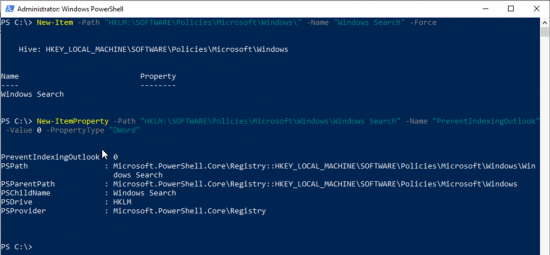
Make Sure Outlook Indexing Has NOT Been Disabled In the Registry
To save you poking about in the Regisry just run the following TWO Powershell commands;
New-Item -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows\" -Name "Windows Search" –Force
New-ItemProperty -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows\Windows Search" -Name "PreventIndexingOutlook" -Value 0 -PropertyType "DWord"
![Enable Outlook Search Registry]()
Microsoft Outlook Repairing PST Files
I detest PST files with a passion! Please stop using them, there’s far more efficient ways of storing old emails for those of you that simply need to keep ‘every‘ email you’ve ever received, sent, or deleted. A broken or corrupt PST file can also break search/indexing.
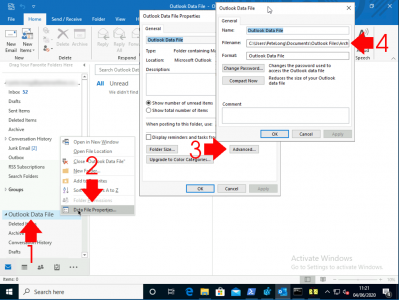
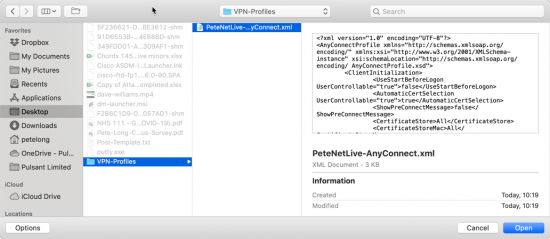
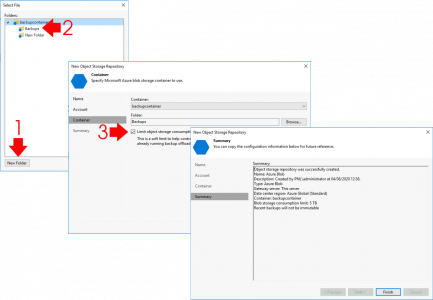
If you are using PST file(s) then firstly you need to know where it/they are. You can get that from their properties > Advanced > Filename.
![Office Locate PST File]()
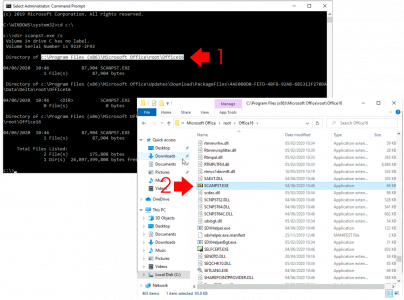
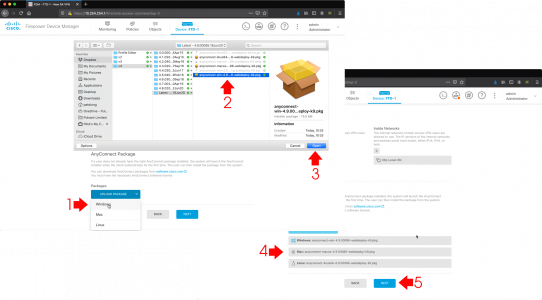
Secondly you need to run the scanpst.exe program to scan and fix them. Each version of Office puts this in a different place annoyingly, but here I’ll tech you some old-school search ninja skills to find it on your PC, (this also saves me listing all the versions and locations, and having to keep updating them!)
Open an administrative Command Window > Execute the following two commands;
cd c:\
dir scanpst.exe /s
After while it should show you where scanpst.exe is, (this is still how I search for files, it’s a lot quicker);
![Office Fix PST File]()
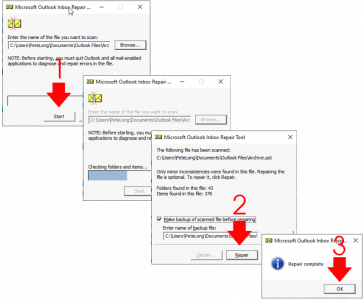
You can now run scanpst.exe and point it at your PST files.
![Office Repair Broken PST File]()
Check Indexing has NOT been disabled by Group Policy
You can get a group policy enforced on you remotely by your IT admins, or on your local PC with local group policy (unless you run a ‘Home’ version of windows where there is no group policy. You can run winver from command line or Powershell and that will tell you, if you’re unsure).
Here I’m going to use Resultant Set Of Policy, to show me the sum total of ALL policies being applied to make sure some doofus hasn’t disabled indexing for the drive/location. My outlook Index should be in (C:\ProrgamData\Microsoft by default, Note: That’s a hidden folder so you may not see it if you try and browse to it).
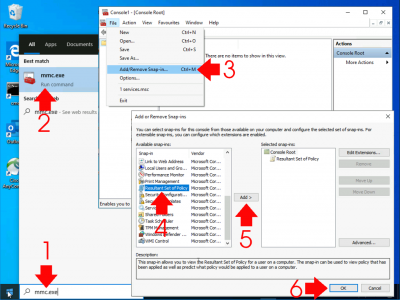
Run > mmc.exe > File > Add/Remove Snap-in > Resultant Set of Policy > Add > OK.
![Resultant Set Of Policy]()
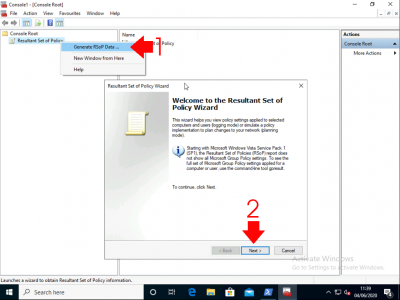
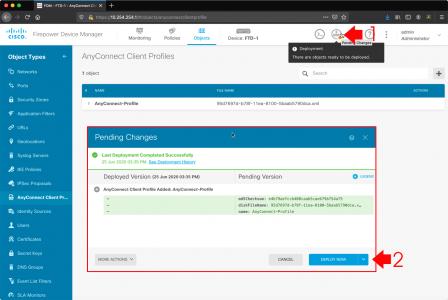
Right click Resultant Set of Policy > Generate RSoPData > Next.
![Generate Resultant Set Of Policy]()
Accept all the defaults (keep clicking next) > Finish.
![Generate Resultant Set Of Policy Data]()
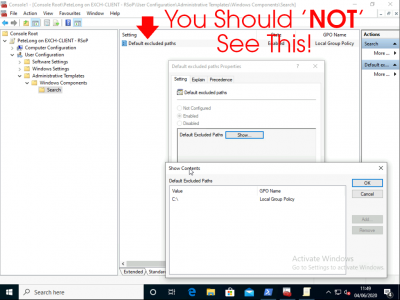
Below, someone has disabled Indexing, (on the C drive!) You should NOT be able to see this. In fact you may not even see administrative templates.
![Outlook Indexing Disabled in GPO]()
Note: Above it’s been set in ‘Local‘ policy, if yours has been set by ‘Domain‘ group policy, you will need to speak to your IT department.
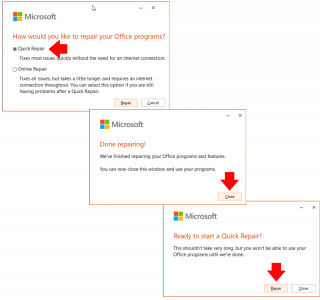
Repair Microsoft Office
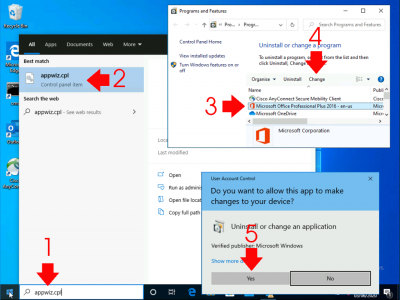
Run appwiz.cpl > Locate Microsoft Office > Change > Yes.
![Office Repair Install]()
Try Quick Repair first (you can rerun and try Online Repair if you wish afterwards) > Repair > Close.
![Office 365 Repair]()
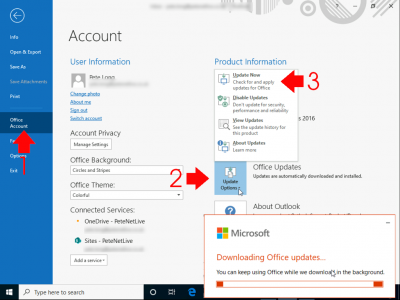
Update Microsoft Office
You should be able to update office from File > Office Account > Update eOptions > Update Now.
![Update Microsoft Office]()
I cant see that option! If you have a retail or volume copy of Windows you may need to manually download the updates. To find out your version of office see the following link;
Finding Out Your Microsoft Office Licence Version
Outlook 2016 and 2019 (Office 365 Version)
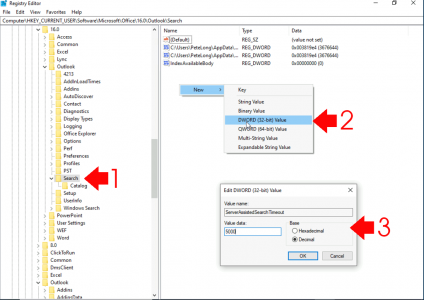
You may need to create a DWORD registry value called ServerAssistedSearchTimeout and set its value to 5000 (decimal), in the following Ley;
HKEY_CURRENT_USER > Software > Microsoft > Office > {version} > Outlook > Search
![Search Broken Office 2016 and 2019 O365]()
Please feel free to comment any ‘fixes’ I’ve missed, below!
Related Articles, References, Credits, or External Links
NA