KB ID 0001474
Problem
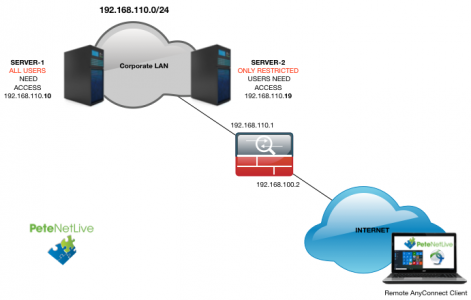
A few years ago I replaced a firewall that was setup like this, and while it took me a while to work out what was going on, I remember thinking it was an elegant solution. Fast forward to today, and I’m now working with the guy who set it up! (Kudos to Paul White).
So when I had a client with a similar requirement, I sat down fired up the lab, and documented it.
What was used;
- Windows 10 Remote Client
- AnyConnect v4 Client
- Server 2016 NAP (NPAS) Server
- Windows 2016 Domain.
- Cisco vASA (v9.2)
Solution
Cisco ASA Configuration
First, configure RADIUS AAA;
!
aaa-server PNL-RADIUS protocol radius
aaa-server PNL-RADIUS (inside) host 192.168.110.19
key 666999
radius-common-pw 666999
exit
!
Create a ‘Pool’ of IP addresses for the remote clients;
!
ip local pool POOL-ANYCONNECT-SN 192.168.249.1-192.168.249.254 mask 255.255.255.0
!
Create some ‘Objects’ one for the Pool you created above, one for the server(s) that everyone can access, and one for the server(s) only restricted users can access;
!
object network OBJ-ANYCONNECT-SN
subnet 192.168.249.0 255.255.255.0
!
object-group network OBJ-USER-ACCESS-SERVERS
description Servers than can be accessed by VPN-USER-ACCESS AD Group
network-object host 192.168.110.10
!
object-group network OBJ-RESTRICTED-ACCESS-SERVERS
description Servers than can only be accessed by VPN-RESTRICTED-ACCESS AD Group
network-object host 192.168.110.19
!
Enable Webvpn and AnyConnect;
!
webvpn
enable outside
no tunnel-group-list enable
anyconnect image disk0:/anyconnect-win-4.6.00362-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-macos-4.6.00362-webdeploy-k9.pkg 2
anyconnect enable
!
Create the ACLs for your TWO AD user groups;
!
access-list ACL-VPN-USER-ACCESS-SERVERS extended permit ip object-group OBJ-USER-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
!
access-list ACL-VPN-RESTRICTED-ACCESS-SERVERS permit ip object-group OBJ-USER-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
access-list ACL-VPN-RESTRICTED-ACCESS-SERVERS permit ip object-group OBJ-RESTRICTED-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
!
Stop NAT being performed on the remote AnyConnect traffic;
!
nat (inside,outside) 1 source static any any destination static OBJ-ANYCONNECT-SN OBJ-ANYCONNECT-SN no-proxy-arp route-lookup
!
Each Group-Policy (below) wont have its own tunnel-group so you need to enable RADIUS on the default web tunnels group, and assign the IP Pool you created (above). Note: I’m allowing authentication to fall back to LOCAL in case the RADIUS server fails;
!
tunnel-group DefaultWEBVPNGroup general-attributes
authentication-server-group PNL-RADIUS LOCAL
address-pool POOL-ANYCONNECT-SN
!
Finally, create a group-policy that the NAP server will tell the ASA to allocate to the users of the AD Groups (VPN-USER)ACCES, and VPN-RESTRICTED-USER-ACCESS);
!
group-policy GP-USER-ACCESS-SERVERS internal
group-policy GP-USER-ACCESS-SERVERS attributes
dns-server value 192.168.110.10
vpn-idle-timeout 30
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ACL-VPN-USER-ACCESS-SERVERS
default-domain value test.net
!
group-policy GP-RESTRICTED-ACCESS-SERVERS internal
group-policy GP-RESTRICTED-ACCESS-SERVERS attributes
dns-server value 192.168.110.10
vpn-idle-timeout 30
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ACL-VPN-RESTRICTED-ACCESS-SERVERS
default-domain value test.net
!
Related Articles, References, Credits, or External Links
Thanks to Paul White and Trevor Stanley.
Windows Server 2016 & 2012 Setup RADIUS for Cisco ASA 5500 Authentication
Windows Server 2008 R2 – Configure RADIUS for Cisco ASA 5500 Authentication
Cisco ASA5500 Client VPN Access Via RADIUS (Server 2003 & IAS)